Mastering Permissions with icacls.exe Command thru the GUI
The key to mastering permissions at the command line in Vista and Windows Server 2008 Server is learning the icacls.exe command. With the introduction of Windows Vista, you can no longer select multiple items like folders and files and apply permissions to a group of objects. The recommended way is to use the command line and the icacls.exe command.
The icacls.exe command was introduced in Windows 2003 Service Pack 2. It now comes installed by default in Windows Vista, Windows Server 2008 (R2) and Windows 7. So administrators will need to learn this command sooner or later. Recently I found the tool to be very flexible and I extensively documented the options. I mapped the different command line options to the GUI, for the network admins that need the GUI to understand how to use the command line.
The first point that should be made about icacls.exe is that it defaults to edit mode. The original cacls command defaults to replace mode. Next are the commands:
/grant will grant user permissions or the add option in the GUI.
/remove will remove the user from the DACL and is equivalent to
the remove option in the GUI.
Note: /remove:g will remove only grants for the user
and /remove:d will remove only denys for the user.
/deny is equivalent to the deny column in the GUI
and should always be used cautiously.
/setowner is a handy little command which allows you to change
the ownership of a file or folder to another user;
this is similar to the linux chown command.
/findsid which finds entries in a DACL for a specified SID or user.
/setintegritylevel is a bit out of the scope of this article
and may be in a future article.
The icacls command also has an /inheritance command which performs the same function as un-checking the “Include inheritable permission from this object’s parent” in the GUI. This of course presents you with the question of how to proceed; copy the permissions or remove all existing permissions. So the command line you can specify:
/inheritance:e to enable same as a check box in the GUI. /inheritance:d to disable and copy the permissions from the parent same as the GUI. /inheritance:r to disable and remove the current permissions again same as the GUI.
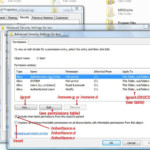
The next thing to learn is how inheritance is propagated for permissions. When using either the /grant or /deny statement you will build the permissions as /grant {user}:{inheritance}{permissions} everything is encapsulated by parenthesis. The default in Windows when applying permissions in the GUI is “This folder, subfolders and files”, but to achieve the default at the command line you need to use /grant {user}: (OI)(CI){permissions} and the permissions should be encapsulated in parenthesis. The table below is to help you formulate your inheritance for permissions:
This folder only This folder, subfolders and files (OI)(CI) This folder and subfolders (CI) This folder and files (OI) Subfolders and files only (OI)(CI)(NP)(IO) Subfolders only (CI)(IO) Files only (OI)(IO)
The last thing to learn is the permissions. You can use macro permissions, which are also called simple permissions or you can use advanced permissions. The simple permissions are the permissions found in the first properties tab under security. The advanced permissions are when you select advanced and you get the full permissions list. So building on the permissions line from above; if we wanted to grant testuser on the folder test and apply modify permissions so all subfolders and files inherited the permissions. The line would be ‘icacls test /grant testuser:(OI)(CI)(M)’
Simple Permissions Full Control (F) Modify (M) Read & Execute (RX) List Folder Contents (X,RD,RA,REA,RC) Read (R) Write (W) Advanced Permissions Full Control (F) Traverse folder / execute file (X) List folder / read data (RD) Read attributes (RA) Read extended attributes (REA) Create file / write data (WD) Create folders / append data (AD) Write attributes (WA) Write extended attributes (WEA) Delete subfolders and files (DC) Delete (D) Read permissions (RC) Change permissions (WDAC) Take ownership (WO)
When you master this command you will be able to do anything with permissions from the command line. Including understanding the SDDL or Security Descriptor Definition Language; which Microsoft uses to create group policy permissions.
October 10th, 2010 at 4:24 am
I need to replaced permission for a user:
I have a folder with a lot of subfolders.
One user have full permission on some of the folders.
I want to remove the full permission access and grant him Modify Permission.
I don’t want to grant him any permission on folder he don’t have permission.
This command will have to run only on folders the user allready exist there, and remove his Full Control…
and Idea what the command needs to be??
October 10th, 2010 at 11:22 am
Hmm… If this is a share why not at the share level just restrict the user to change permissions. In effect the combined (groups) NTFS permissions will give him the most permissive and the combined share permissions will give the most permissive. However the combination of the resultant NTFS permission and share permission will be the most restrictive. In example of:
Joe (member of HR & Sales)
NTFS permissions:
Joe – Full
Sales – Change
HR – Read only
Share permissions:
Joe – Full
In effect Joe has Full control, however if the share permissions are changed to Change then Joe will have no more than Change permissions. Most restrictive of the combined NTFS and Share. I do not know of a way to replace selective permissions, other than switching the existing permissions for a user. Substitute one user for another, but not one permission for another. The other problem is that if the user is the owner of the file they retain FULL permissions regardless, which makes the share level restriction more attractive. Since regardless if the person owns the file and has FULL rights the share blocks that to change. I have found no other problems with doing that in the past 12 years with NTFS and Share, no problems even with software running from shares.
March 7th, 2011 at 12:10 pm
Thanks for this article! First one I have found re: inheritance of permissions. I am trying to finish up a script that creates a folder structure and assigns permissions via icacls. I have the script working correctly except for one thing. When setting permissions with iCacls the folders have inheriting permissions set on. I want the permissions to be only set for that folder only and not inheriting to the child folders/files or inherited from the parent. Currently the command that I am using is:
intRunError = objShell.Run(“%COMSPEC% /c Echo Y| icacls ” & strFolderPath & ” /c /grant Administrators:(NP)(RX) /inheritance:r “, 2, True)
I thought that the (np) setting would do the trick but no love…. and in your article I was very interested in the /inheritance:r switch. I tried it right after the folder path and just before the user and after the user and I am getting errors. I don’t have much experience using icacls and would appreciate any insight on how to prevent inheritance of permissions when creating folders(w/vbscript) and assigning permissions with iCACLS. A full explanation (working example!!!) on how to do this would be enlightening as I can’t find a clear description (for me at least) of how to do this task.
March 7th, 2011 at 1:02 pm
Dan,
I am not sure… In reading your post it looks like you have a syntax error. You are on the right track… My suggestion is to create the permission structure and then use the export feature using the /save switch to read the SDDL or Security Descriptor Definition Language. SDDL is what is used to create ACEs (Access Control Entires) in the DACL (Discretionary Access Control List). So I think the key for you is to understand the SDDL a little better. Check out the article of http://www.netid.washington.edu/documentation/domains/sddl.aspx. I was looking for a vbscript I used in the past to create ACEs and DACLs, however it had no control on the inheritance. I think I modeled the code from a vbscript that was included with one of the older NT Resource Kits (2000?). I might have even taken the code from 4 guys from rolla. However you are on the right track with the shell to icacls.
Jon
September 9th, 2011 at 5:08 am
How to achieve this concept for non NTFS (for Eg. USB drives)
September 13th, 2011 at 1:16 am
How could I use icacls to set permissions on multiple folders named “other” which is two sub folders deep? So folder 1>folder A>other, folder 120>folder B>other so all other folders would get the permissions set by icacls.
Thanks,
Matt
September 13th, 2011 at 8:24 am
Unfortunately NTFS is the only file level security that Windows supports. If you are dealing with removable storage of a sensitive nature I recommend using TrueCrypt. Create a crypt file on the base of the UFD (USB Flash Device) and then just mount it when needed. I keep all of my uber secure information on a UFD and never worry about loosing it, since if it’s lost the person would need to identify the file and break the AES256 encryption. If you’re storing sensitive information on UFD without using TrueCrypt, your information will be stole at some point. Yes TrueCrypt is totally FREE!
October 4th, 2011 at 5:06 pm
It’s a sad day for me. Logging on to my Win 7 system, I found I had no task bar icons, no desktop icons and no files in my start folders. Definitely not good!! Upon investigation, I found that the files and objects were there but hidden, and found that I could not unhide them. After many hours of attempted to repair, I chose to rebuild my system. In order to save my data, since I am the only user on this desktop I bought a new 1TB drive, formatted and partitioned it, and “rolled” off all my data to the new HDD.
My problem is all the data on the new drive is in the same state, read only and hidden.
Since we are talking about 100,000 files, mostly images, docx and xls files, is there a way, using takeown and icals to set these files back to “factory” ownership and permissions. Is it as simple as:
icacls * /T /Q /C /RESET
but what ARE those permissions and who would the owner be.
Also what are the “standard” security characteristics.
bob
October 4th, 2011 at 6:54 pm
That is two questions… First what do the switches do? and the other is what are the defaults? First the icacls * means all matching files the “/T” tells it to carry the function out on all file and subfolders below and the “/Q” and “/C” is to suppress errors and not print messages to the console on success. The “/reset” will carry the inherited permissions all the way down and forcefully reset permissions. Now the second question is what are the default install permissions? In Windows XP it use to be applied during setup, but since Windows Vista and Windows 7 use WIM file the permissions are applied as the files are expanded. However defltbase.inf still exists and can be used to reapply permissions in Windows 7 back to “factory” permissions; using the command of “secedit /configure /cfg %windir%\inf\defltbase.inf /db defltbase.sdb /verbose” the inf file is in “c:\windows\inf”. This is the proper procedure to reset permissions back to default.
October 4th, 2011 at 10:29 pm
Thanks for the timely reply and your insight Jon.
The reason that I was considering icals in lieu of secedit was the KB Article ID: 313222 – Last Review: September 23, 2011 – Revision: 15.0. It said:
“The use of “secedit /configure” to import the default security template, dfltbase.inf, is unsupported nor is it a viable method to restore default security permissions on Windows Vista, Windows 7, Windows Server 2008 and Windows Server 2008 R2 computers.”
The same article said that using icacls /restore would be good. The problem is, you must have a previous backup from the icacls /save command. I do not have one or know of one, but I would assume that there would be some file that would have the “initial” settings employed an admin or user creates the first folders in a disk or partition. Whatever is assigned during that creation would be the “basic” settings, that would subsequently be manually modified by a user, if desired.
Right now, the only idea I have is to go to another satisfactorily operating Win 7 computer and to perform an icacls /save and then copy that file to this computer. The problem is that the restore affects all partitions and disks whereas I only want to modify the disks containing my copied files (rescued from my system prior to the rebuild).
Is there such a basic set of simple/advanced permissions that are available?
December 1st, 2011 at 2:04 pm
I have a very simple example I’m hoping someone can provide the solution for. I want to use the “icacs” utility to grant Full Control to a couple Excel files on the local hard drive to ONLY the logged in user on a Windows 7 desktop (eg, %USERNAME% environment variable), and NO access to anyone else. How would I accomplish this? It seems there are a lot of default user groups that get access by default but I want to remove these (eg, “NT AUTHORITY\Authenticated Users”, “BUILTIN\Administrators”, “BUILTIN\Users”, etc).
December 2nd, 2011 at 4:09 am
I want to do something like amir (1st post).
We have a badly maintained dacl structure with ad hoc added users and groups everywhere.
Now somehow the local users group has read rights inherited through the whole tree. We don’t want that!.
I can’t block inheritence, remove the local users group and propagate this to all child objects, because I lose all the ad hoc users and groups!!!!
Question; how can I remove only the specific group from all acl’s troughout the tree while preserving the rest of the settings.
December 2nd, 2011 at 8:49 am
Personally I would go back to basics with the original cacls command. cacls /e for edit will do what you are looking to do. It will edit the DACL in stead of replacing it, so you will retain the original permission structure. Coupled with the /r or revoke that should do it. I would test it first and there is probably a way to do it with the icacls command, but at first glance I didn’t see how. Why waste the time if the cacls command will work.
December 15th, 2011 at 1:08 am
I believe the following line above is incorrect:
Subfolders and files only (OI)(CI)(NP)(IO)
When I use the above it gives lower folders “Subfolder only” permissions, which is different from when choosing “subfolder and files only” via the GUI. I found the following line works the same as the GUI:
Subfolders and files only (OI)(CI)(IO)
cheers
PS. Otherwise this has been one of the more useful ICACLs related pages that I have read (and I have read lots).
February 3rd, 2012 at 2:47 pm
Need some help please:
This work cacls “C:\Program Files\XXXX” /e /g “Domain\domain users”:C
for the first folder not for sub folder
How do have add “domain users” to the all the subfolder and files Using Icacls
February 3rd, 2012 at 5:52 pm
Use a /t which changes DACLs of specified files in the current directory and all subdirectories.
cacls “C:\Program Files\XXXX” /e /t /g “Domain\domain users”:C
I do it all the time…
Depending on the files you have you may which continues to change DACLs, ignoring errors.
March 7th, 2012 at 5:18 pm
I am having a problem with a simple batch file to create and then assign permissions to user home folders on a NAS device.
The batch file is:
for /f %%a in (users.txt) do (
md \\nasdevice\home\%%a
icacls \\nasdevice\home\%%a /grant %%a: (D)
)
The users.txt file simply creates a list of usernames. The folders are created but when it attempts to set permissions it displays the error:
Invalid parameter “:”
It does display the correct username. I read that icacls may not work on network shares but could not confirm. Any ideas??
Thanks
May 14th, 2012 at 5:33 am
Hey Bob Broccoli, aren’t you looking for this command instead?
ATTRIB *.* -S -H /S
This will remove the “hidden” attribute from all the files in current directory and subfolders, even if they have the “system” attribute on.
May 14th, 2012 at 6:00 am
And Don, it looks like you have an extraneous space between “%%a:” and “(D)”. There shouldn’t be any: “%%a:(D)”.
June 25th, 2012 at 10:30 pm
How could I put this into a batch file that could be run from a USB drive? The USB has the NTFS file system. Any idea?
I want to make a folder that when unlocked the everyone group has full control but when it is locked the everyone group has no access to it. This should also apply to every user group so admin, standard, limited etc
June 26th, 2012 at 6:00 am
Not sure it sounds like you want to do something unique like toggle user to install fonts. There may be something creative with GPO that you could do, but I do not believe the controls exist yet. Another alternative would be to use GPO to administratively install the fonts, since it will run under the context of system if it is assigned to the computer.